Vulnerability Lifecycle Management Platform
Track and manage vulnerabilities from discovery to closure with PentestHub's end-to-end lifecycle platform. Monitor fix status through five stages, automate assignments, track remediation progress, and ensure verification with intelligent workflows, automated notifications, and complete accountability.
Centralized Vulnerability Repository
Centralize all vulnerabilities across web applications, APIs, servers, and network devices in one unified platform with automated scanner integrations and real-time dashboards
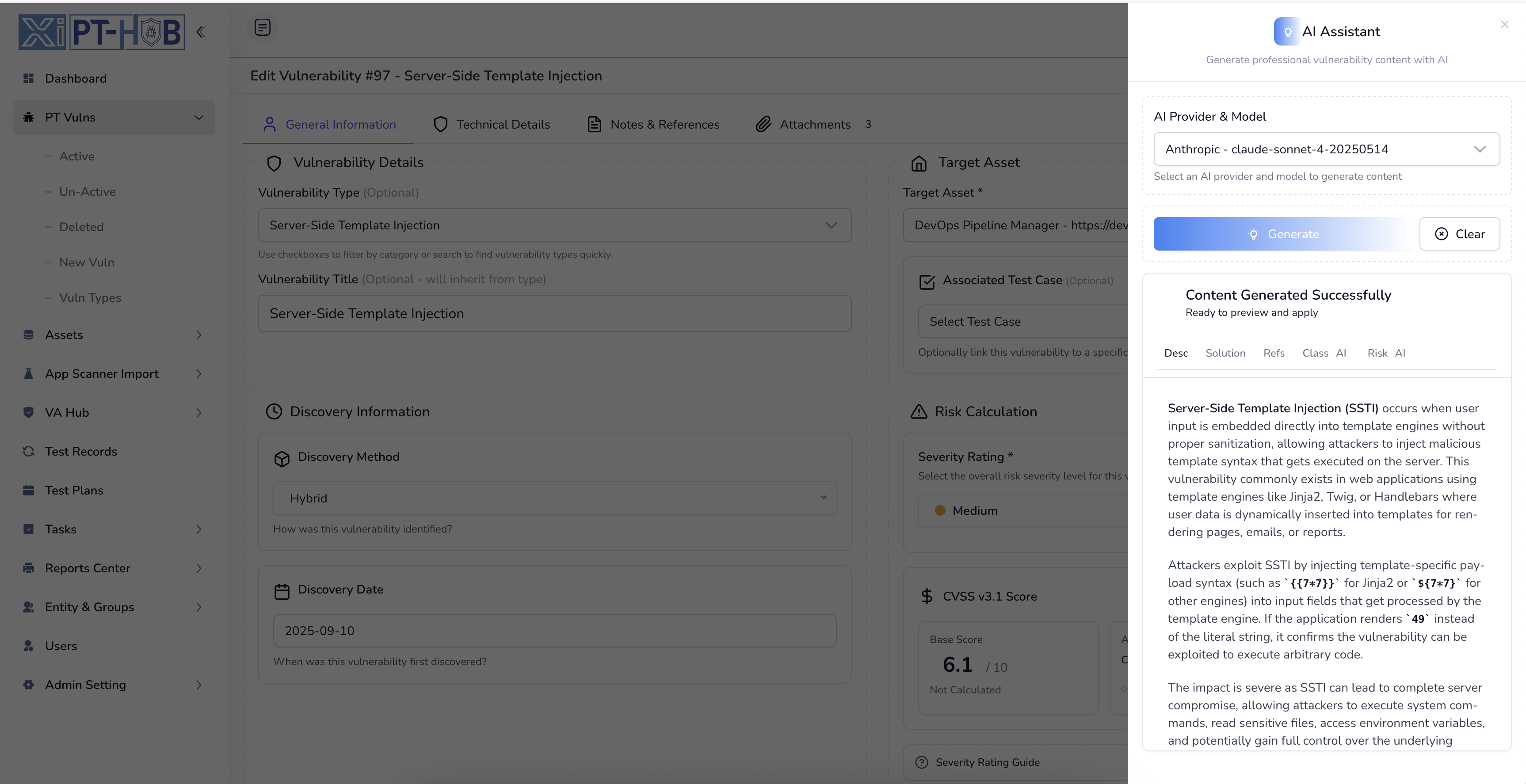
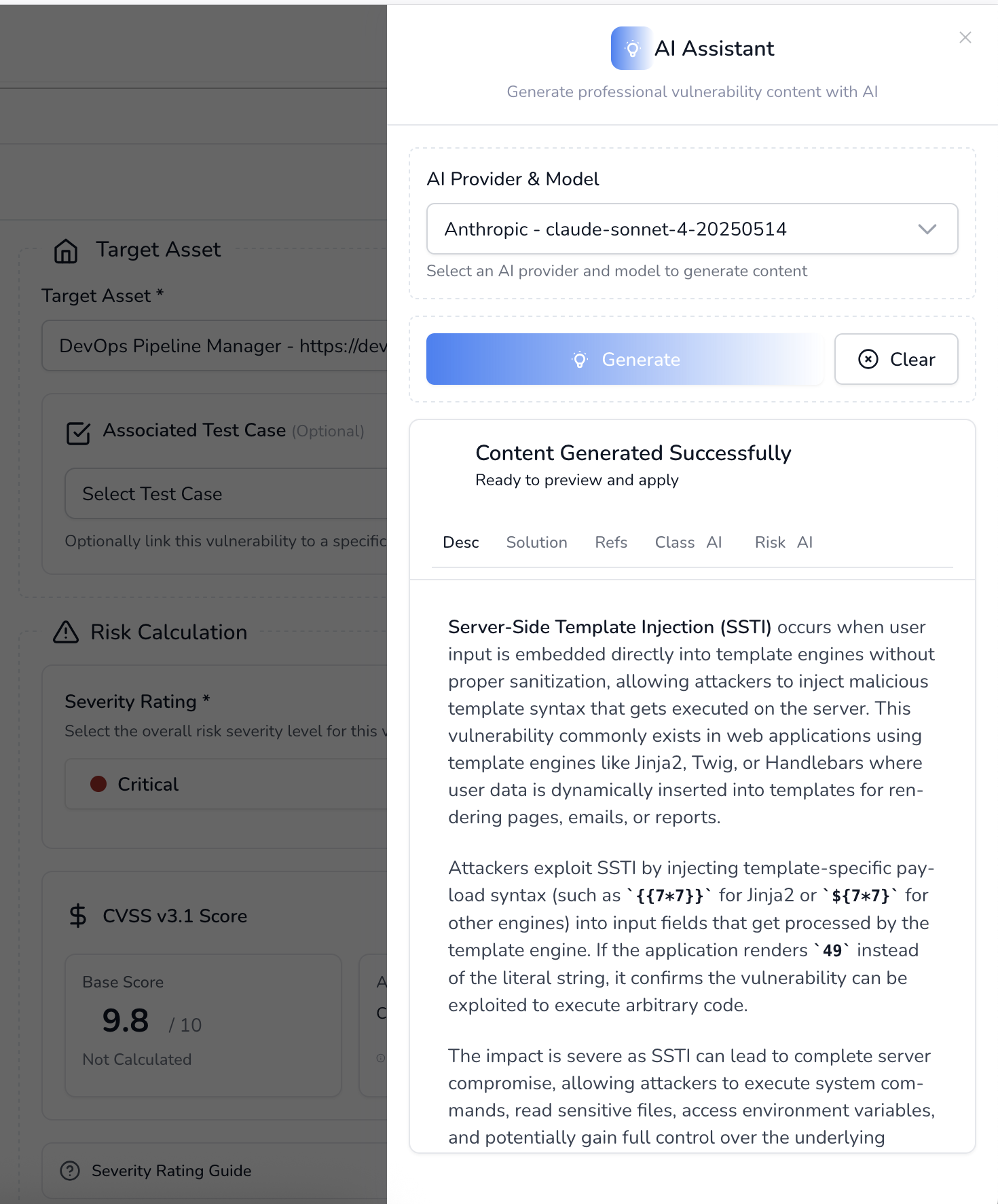
AI-Powered Vulnerability Intelligence
Leverage advanced AI to accelerate vulnerability analysis with automated descriptions, CVSS scoring, classification, and intelligent remediation recommendations
Professional Vulnerability Reporting
Generate comprehensive vulnerability reports with OWASP Top 10 mappings, customizable PDF templates, executive summaries, and detailed findings with severity analysis
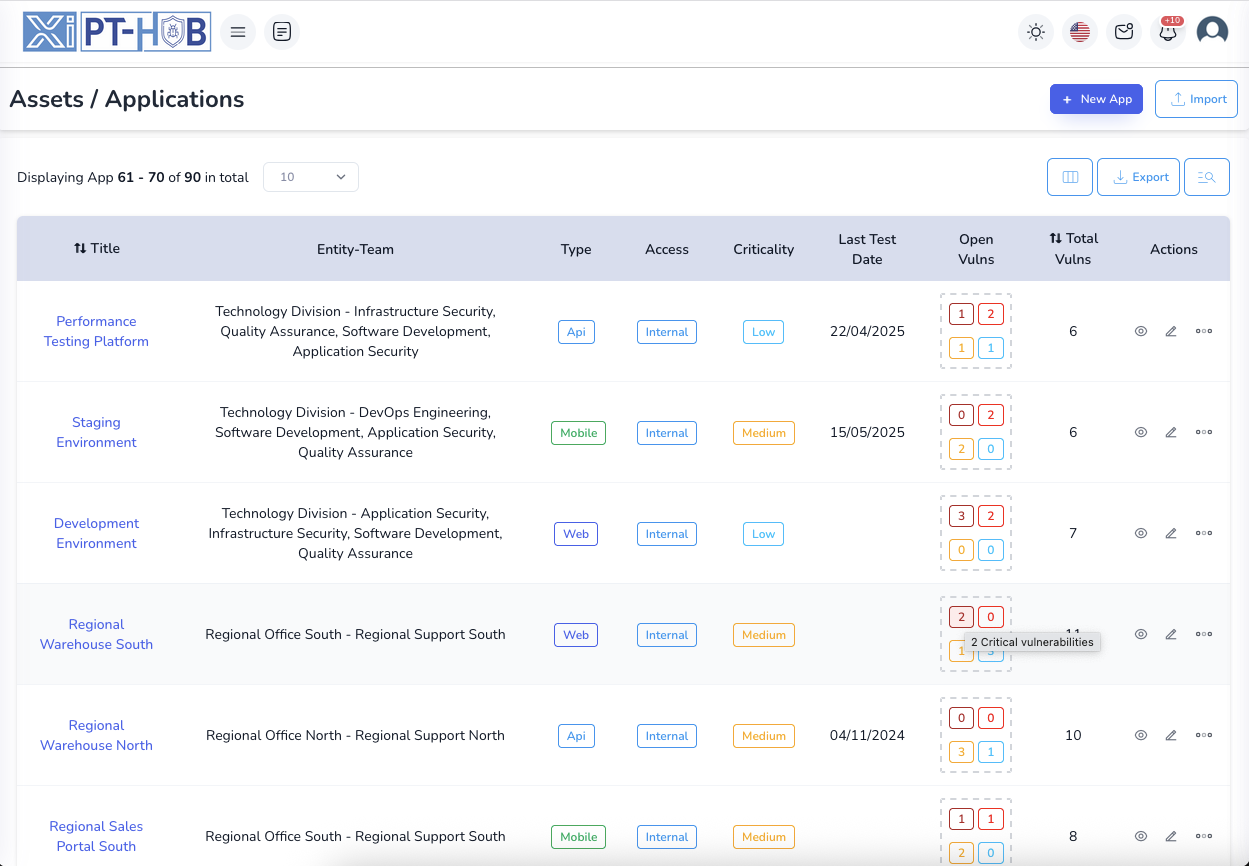
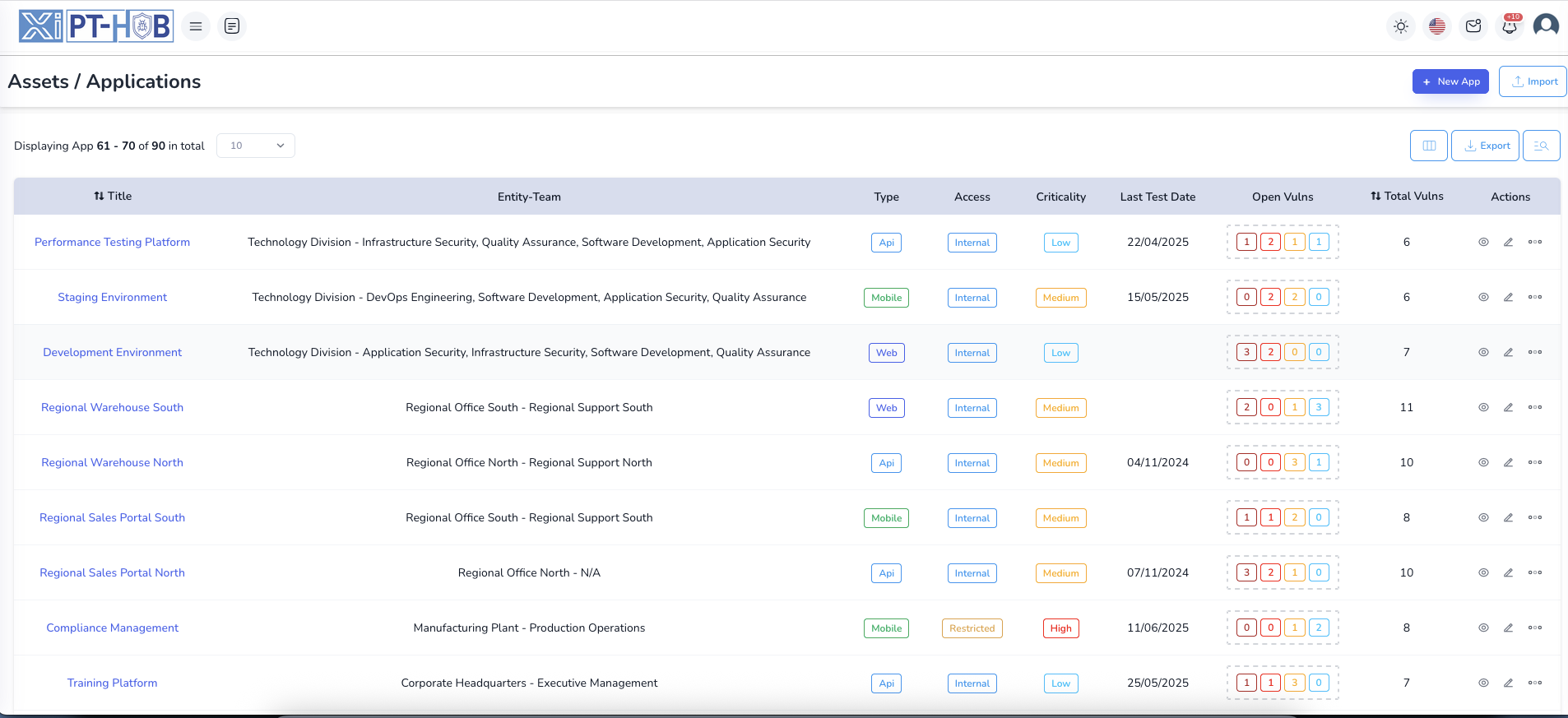
Comprehensive Asset Inventory & Management
- Centralize your entire IT asset inventory with support for web applications, APIs, servers, and network devices in a unified platform with detailed asset profiling and relationship mapping
- Track asset criticality levels, ownership assignments, technical specifications, and business context including frameworks, operating systems, firmware versions, and deployment environments for complete visibility
3
Asset Types
Applications, Servers, and Network Devices in one platform
100%
Asset Coverage
Complete visibility across your entire infrastructure
End-to-End Vulnerability Lifecycle Platform
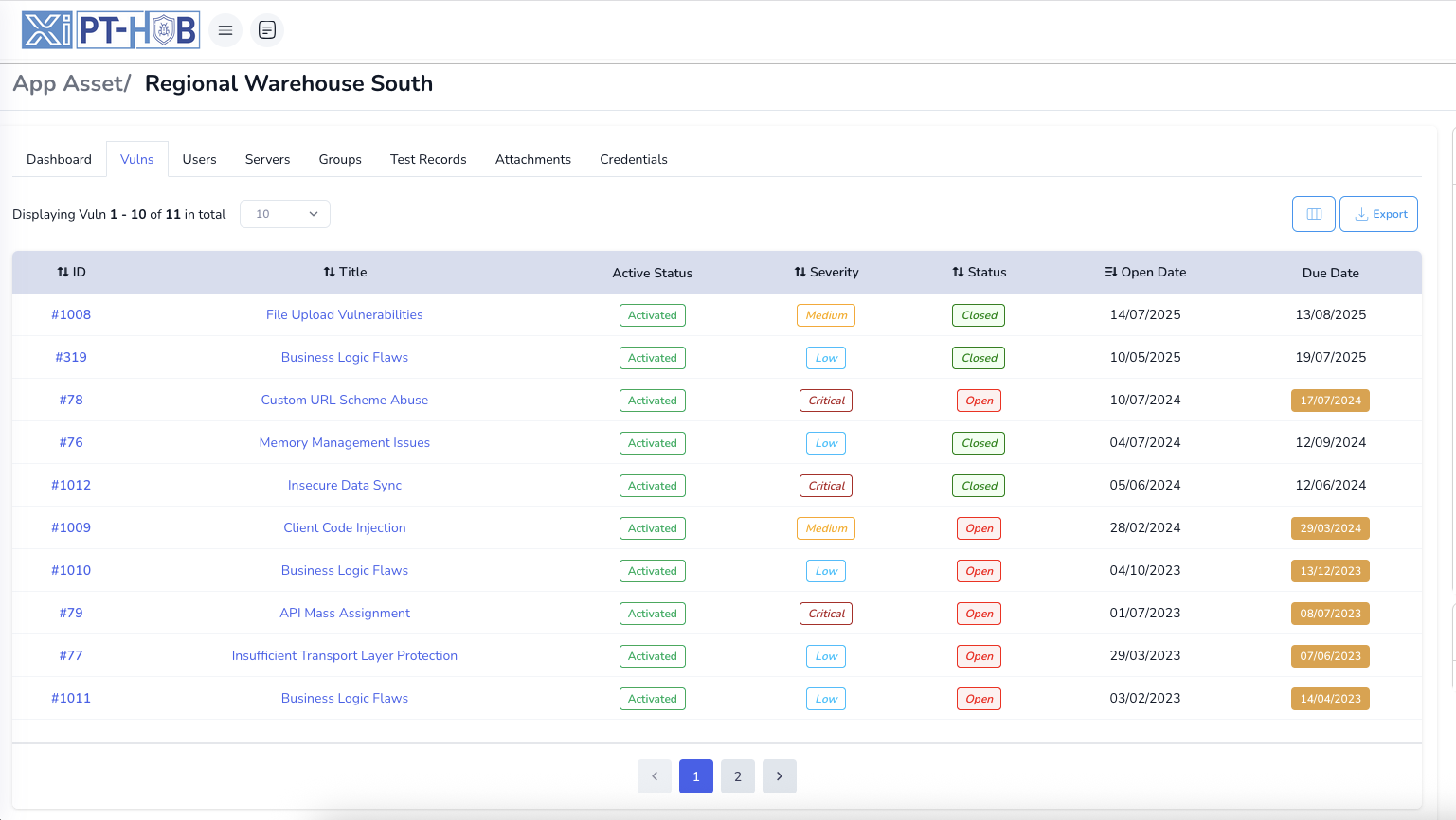
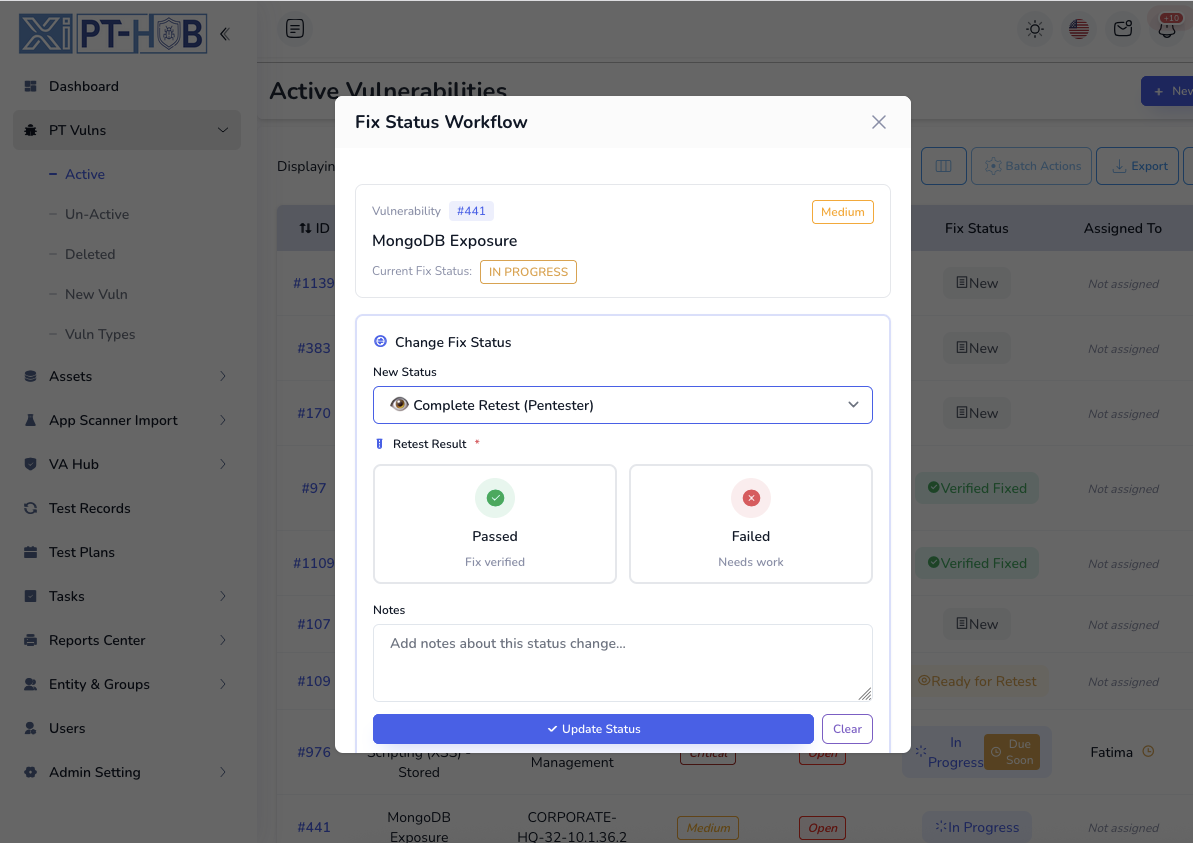
Discovery to Closure Tracking: Manage the complete vulnerability lifecycle from initial discovery through assignment, remediation, verification, and closure with comprehensive tracking at every stage, ensuring complete accountability and nothing falls through the cracks
Five-Stage Fix Status Workflow: Track remediation progress systematically through New → Assigned → In Progress → Ready for Retest → Verified Fixed with automated status transitions, assignment notifications, deadline tracking, and complete audit trails at each stage
Automated Lifecycle Management: Streamline workflows with automatic scanner imports, intelligent deduplication, priority-based assignment, SLA monitoring, retest management, and verification workflows—all integrated in one unified platform
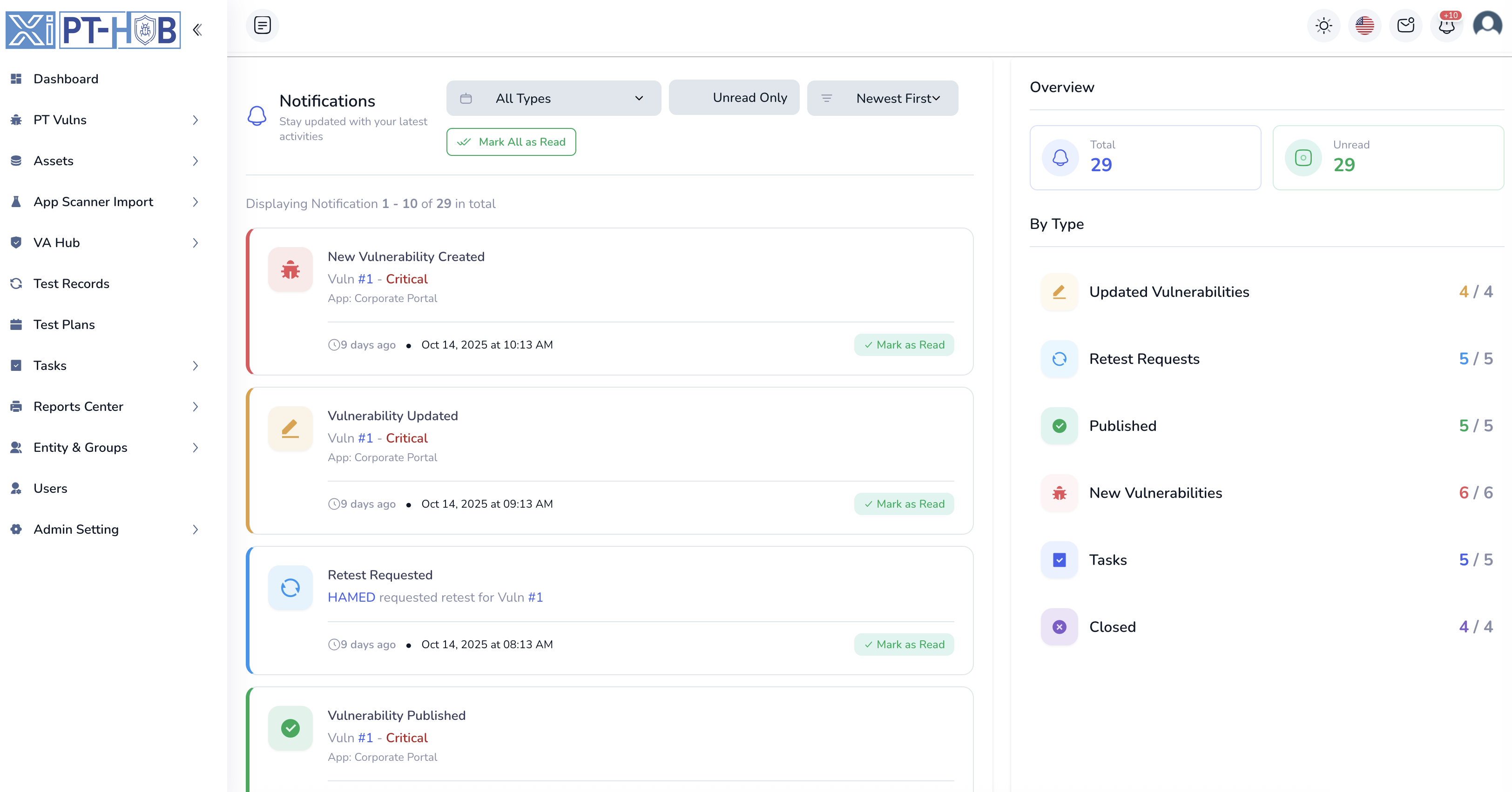
Instant Alerts & Multi-Channel Delivery
Vulnerability Alerts: Instant notifications when new vulnerabilities are discovered, imported from scanners, or assigned to your team. Get real-time updates on critical findings with severity-based priority alerts
Workflow Updates: SLA Deadline Alerts: Automated reminders for approaching remediation deadlines and overdue vulnerabilities. Stay compliant with configurable warning thresholds and escalation notifications
Multi-Channel Delivery: Receive notifications via in-app alerts, email digests, and webhook integrations to Slack, Teams, or custom endpoints with granular preference control
Enterprise-Grade Vulnerability Management Features
PentestHub provides comprehensive vulnerability management capabilities designed for modern enterprises, from automated discovery and intelligent prioritization through remediation tracking and professional reporting
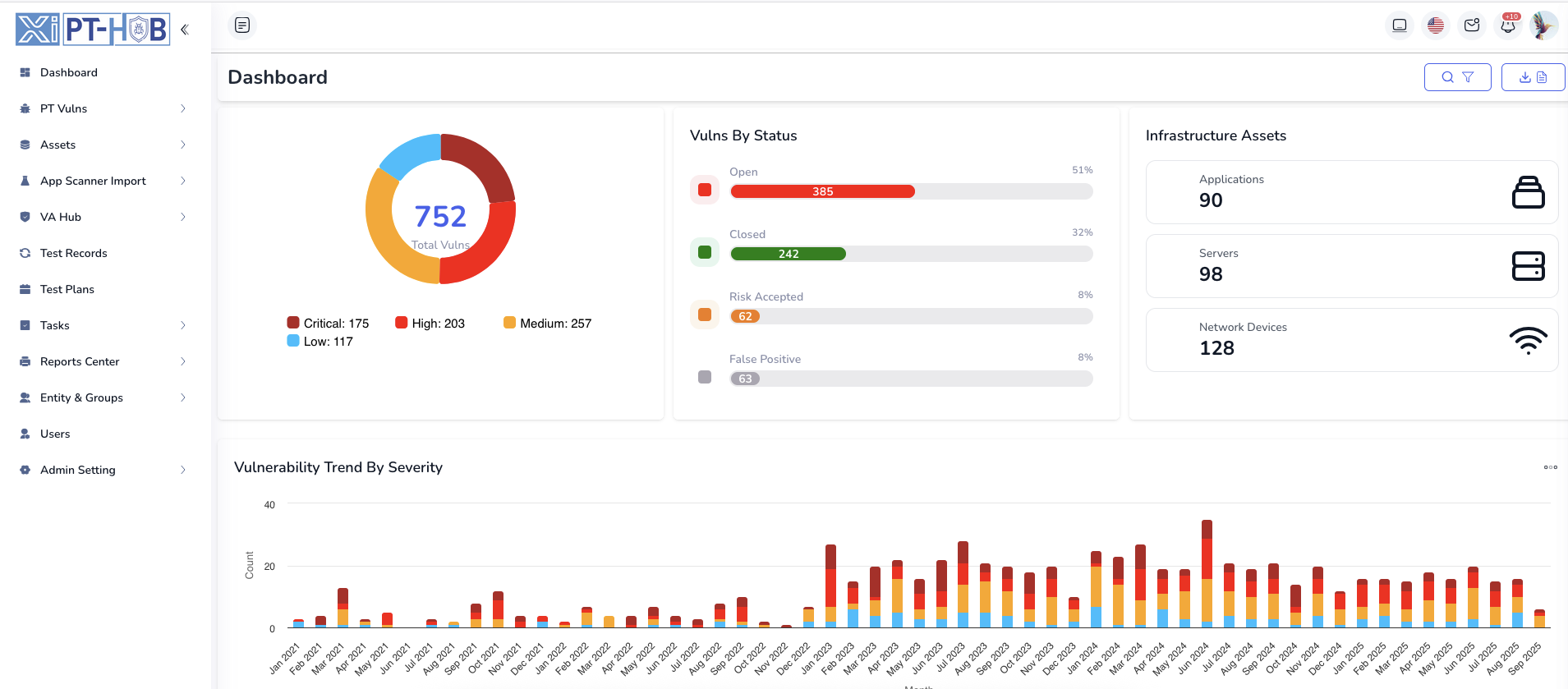
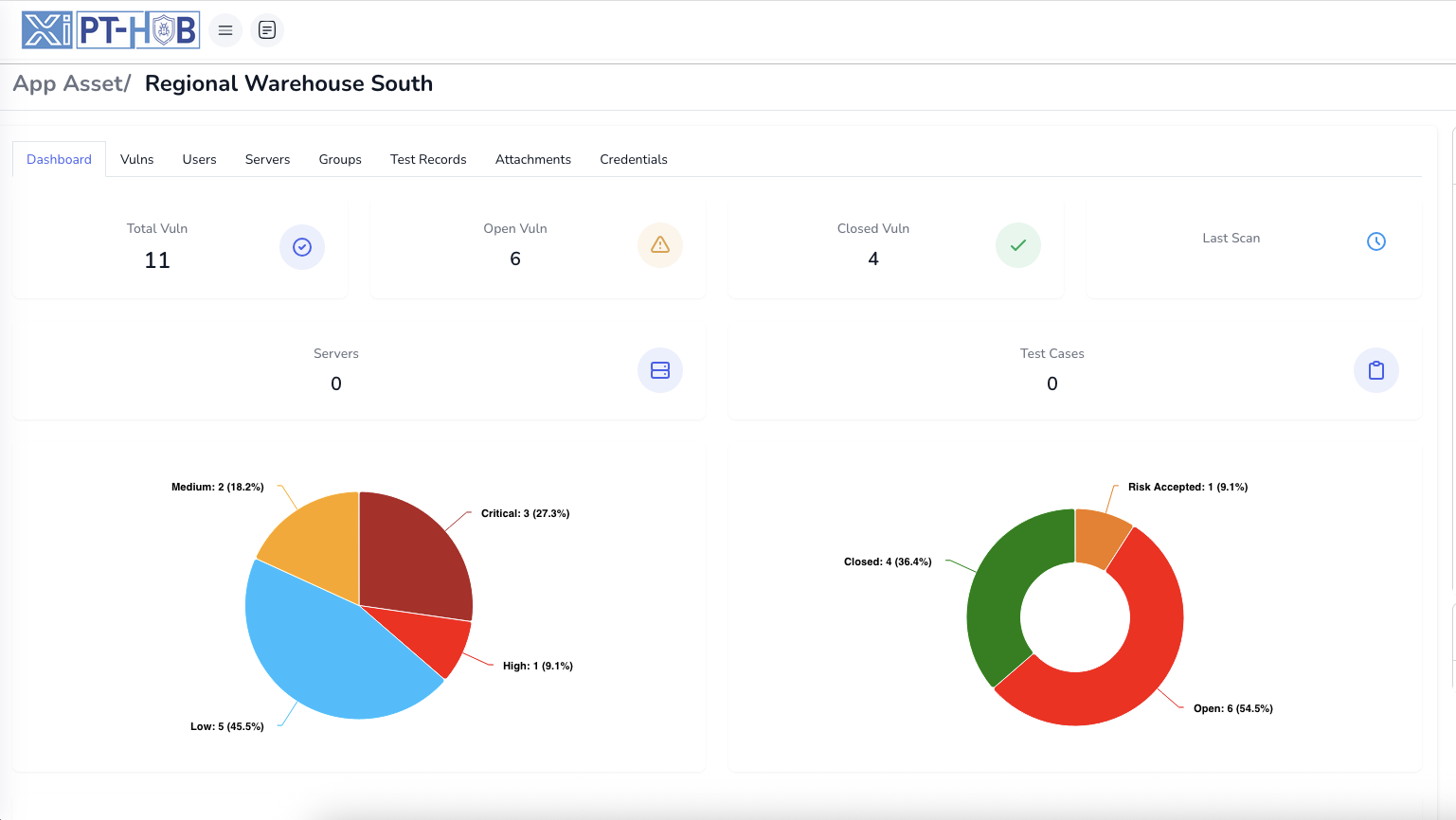
Real-Time Vulnerability Dashboards
Gain complete visibility into your vulnerability landscape with real-time dashboards tracking vulnerability trends, severity distributions, remediation metrics, and SLA compliance across all assets with customizable widgets and executive-level reporting
Intelligent Notifications & Alerts
Stay informed with real-time email and in-app notifications for new vulnerabilities, status changes, assignment updates, SLA breaches, and approaching deadlines. Customize notification preferences by role, severity, and event type for effective team coordination
CVSS Scoring & Intelligent Prioritization
Automatically calculate CVSS v3.1 scores with interactive vector editors. Intelligently prioritize remediation efforts based on severity, asset criticality, business impact, and exploitability with AI-powered risk assessment and contextual analysis
Team Collaboration & Assignment
Streamline vulnerability remediation with team-based workflows, intelligent assignments, comment threads, and complete activity tracking. Enable seamless collaboration between security teams, developers, and operations with integrated communication and escalation workflows
Multi-Tenant & Role-Based Access
Enterprise-ready multi-tenant architecture for MSSPs and large organizations. Complete data isolation by entity with granular role-based access control, custom workflows, white-label reporting, and independent branding for each tenant
Asset & Scanner Management
Centralize asset inventory across web applications, servers, and network devices. Integrate with multiple vulnerability scanners (Nessus, OpenVAS, Qualys, Tenable, Acunetix, Burp Suite, Fortify, OWASP ZAP) for automated import, intelligent deduplication, and unified vulnerability tracking
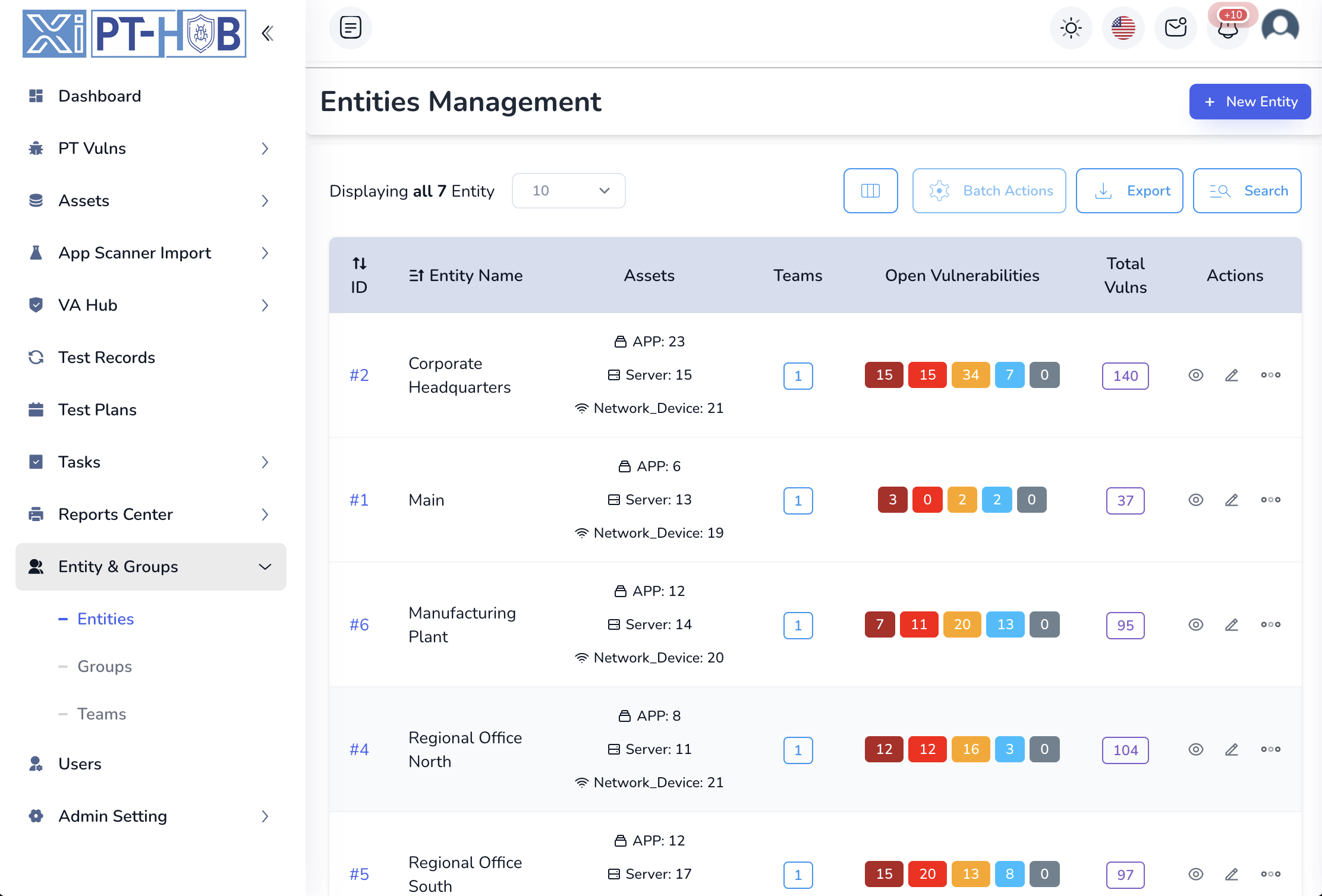
Enterprise Team Collaboration & Multi-Tenant Architecture
Team-Based Collaboration: Organize users into teams with asset ownership, vulnerability assignments, and collaborative workflows. Enable seamless communication between security teams, development teams, and business units with integrated comment threads and real-time notifications
Entity & Group Management: Structure your organization with entities, groups, and teams. Map assets to business units, assign ownership, and maintain clear organizational hierarchy with entity-based access control and visibility management
Multi-Tenant Isolation: Enterprise-ready multi-tenant architecture with complete data isolation between organizations. Perfect for MSSPs, security consultants, and large enterprises managing multiple subsidiaries with independent branding, workflows, and user bases
Granular Role-Based Permissions: Control access at every level with role-based permissions, team-specific visibility, and custom permission sets. Restrict users to their own vulnerabilities, team assets, or entities with flexible access control policies
AI-Powered Vulnerability Intelligence & Automated Remediation
Leverage cutting-edge artificial intelligence to accelerate vulnerability analysis, prioritization, and remediation. Our AI engine analyzes thousands of vulnerabilities, provides context-aware recommendations, and generates intelligent fixes tailored to your specific environment.
Smart Vulnerability Analysis: AI examines CVE details, exploit availability, and environmental context to provide accurate risk scoring and remediation priority
Automated Fix Generation: Generate code patches, configuration changes, and remediation steps automatically based on your technology stack and security policies
Intelligent Insights: Get AI-powered recommendations for vulnerability patterns, attack surface reduction, and proactive security improvements
Ready to Transform Your Vulnerability Management Operations?
See how PentestHub can streamline your vulnerability management and remediation workflows